Security Operations Center
It’s not the size nor the aesthetics of your organization’s Security Operations Center (SOC) which makes it efficient – it’s the intelligence. Consolidating systems into one unified platform not only drastically increases the operator’s ease of use, but eases the management and on-going maintenance as well.
Providing operators with pre-qualified notifications from multiple simultaneous input sources ensures the right information is provided to the right person at the right time – every time.
“Video data is only as powerful as the tools used to provide actionable intelligence to the right people at the right time.”
A Single Platform That Evolves With You
We offer a truly unified SOC platform that blends IP video surveillance, access control, automatic license plate recognition, intrusion detection, and communications within one intuitive and modular solution. By taking advantage of a unified approach to security, your organization becomes more efficient, makes better decisions, and responds to situations and threats with greater confidence. Plus, operators enjoy the same, intuitive user experience across your entire security system – from system configuration and management, to live monitoring, reporting, and mobile access.
Reliable and Cybersecure
Built-in failover and redundancy work to safeguard system access, limit interruptions, and ensure your system is always available. Advanced security mechanisms (encryption, authentication, authorization) protect privacy by preventing unauthorized access to sensitive data.
Flexible and Scalable
Through its open architecture, you can enhance Security Center with modules and 3rd party add-ons that suit your business’s changing needs. It seamlessly scales to hundreds of sites, and thousands of cameras, doors, intercom devices, and intrusion panels.
Efficient Deployment and Maintenance
With a unified approach to security management, organizations experience real savings in deployment, maintenance, training, and day-to-day management of security. Plus, you avoid the compatibility issues typically faced with the integration of multiple independent products.
A Clear Path to the Cloud
Extend the capabilities of your on-premises installation and reduce IT infrastructure costs with our cloud services. With Security Center SaaS edition, cloud archives, automated updates and health monitoring, your organization becomes more agile and less dependent on hardware.
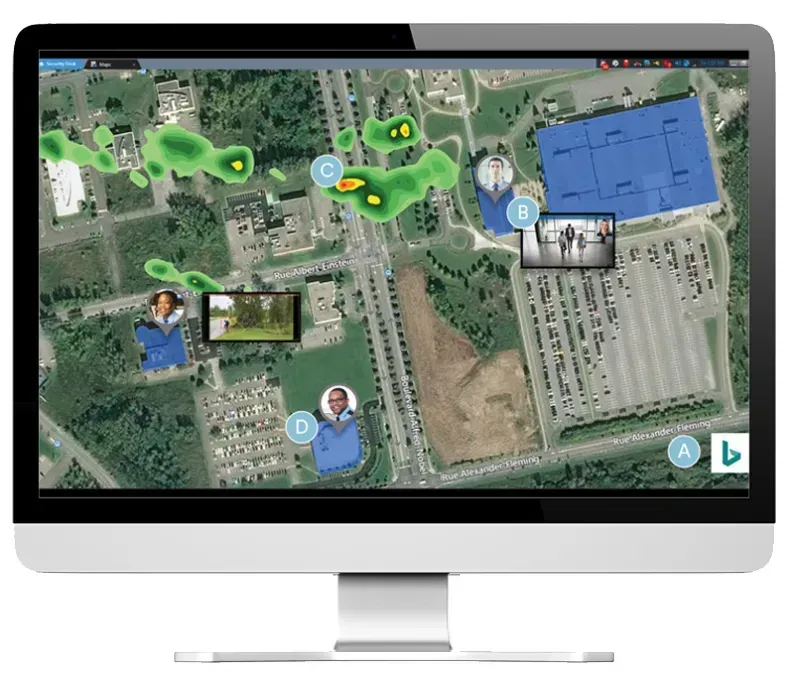
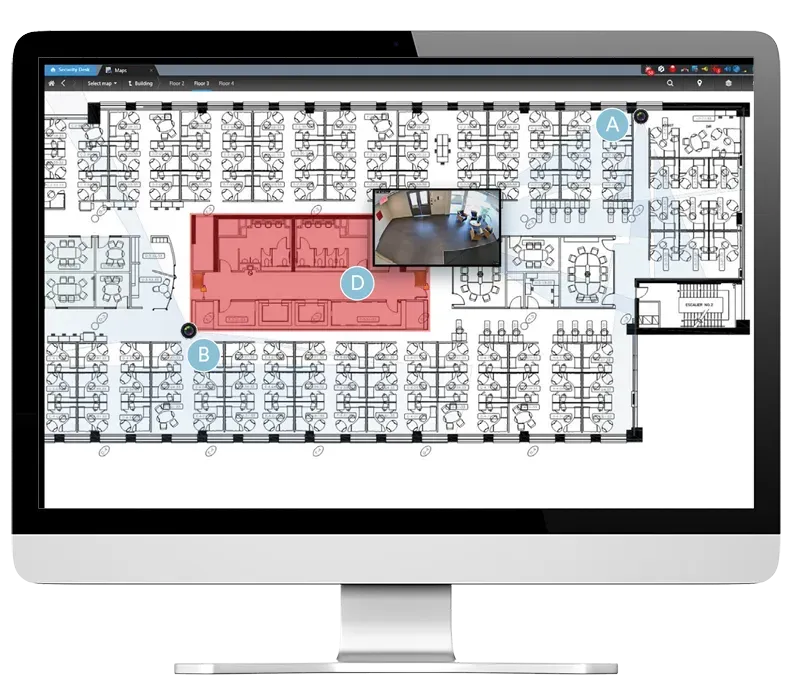
See and Respond to Events in Context
Our unique, interactive mapping module delivers a complete map-based monitoring solution. It helps you visualize events, locate security devices and operators close by as well as pull up cameras, unlock doors, or activate other devices – all from the same interface. From a single monitoring application at their workstation or in a security operations control room, operators view the entire security environment.
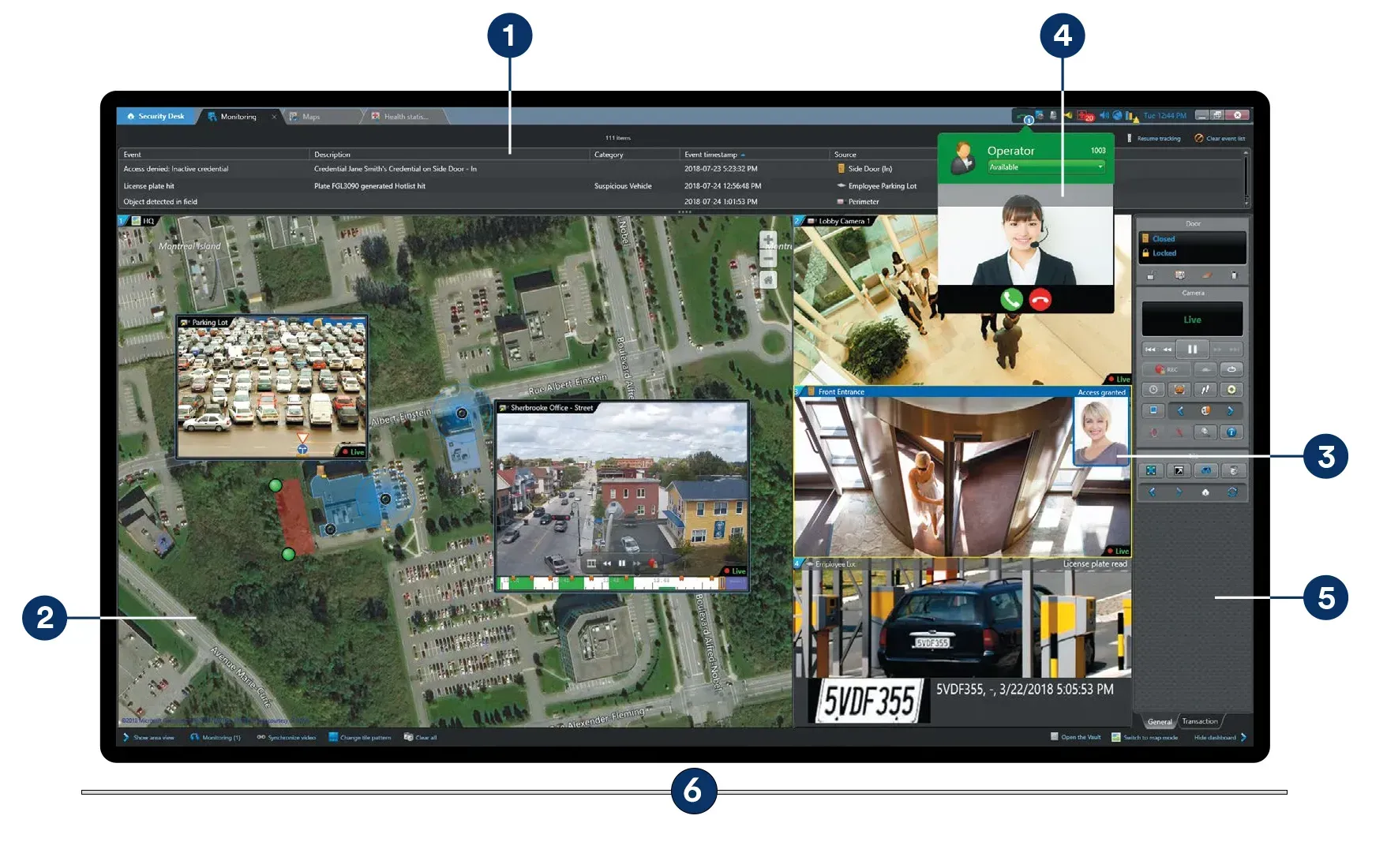
1
Live Monitoring and Cardholder Verification
Perform monitoring and reporting tasks in multiple tabs so you can instantly go back to the previous operation at hand.
2
Interactive Maps
Seamlessly monitor and navigate through buildings using hot spots and the floor selection tool that displays real-time events and status updates, along with the location of events, alarms, doors, and devices on geographical maps and floor plans.
3
BIOMETRIC Cardholder Verification
Cameras, doors, automatic license plate recognition units, intercoms, and other security devices can be operated without changing tasks. Cardholder identity (picture) authentication is made against live or recorded video.
4
Embedded Communication
The location of mobile app users is also shown in real-time, with the ability to send and receive messages, call, or share video clips with other operators or intercom stations, directly from the Security Center interface.
5
Dynamic Dashboard
Built-in data layer support displays relevant information from external systems, enriching operator comprehension so they can quickly take action through an adaptive dashboard that automatically displays commands and controls associated with the currently selected camera, door, or area.
6
Comprehensive View of Your Security Operations
Locate alarms, activate and monitor intrusion areas, and initiate a response directly from maps. Rapidly identify available cameras with live field-of-view tracking.
Planning is the most underestimated part of security system design.
We understand the complexities and requirements for a well-planned and designed security system. Colorado-based Confluence Security is here to assist in creating or updating your advanced layers of security, augmenting your existing security systems, and enabling ProAction!
The planning stage uncovers much of the automation to be incorporated, but what about additional steps to ensure appropriate resolution?
Establish Standard Operating Procedures (SOP’s)
By implementing new or existing Standard Operating Procedures (SOP’s) in response to any given situation, operators can follow an instruction set for each scenario.
Create a Decision Support System
Employing a powerful and well-defined Decision Support System powered by automation provides simple guidance, pausing at decision points to await input from operators, while reducing the likelihood of human error.
Establishing Proactive Security Operations
Empowering security teams to take proactive action — what we call ProAction!
Security and safety teams come in all shapes and sizes, and rarely share commonalities with other businesses, even in the same industry. We understand every organization’s needs are unique. Proper planning is paramount to our process. Identifying all the potential resources and where they reside within the organization assists in the categorization of responsibility to ensure applicable training is maintained and any hardware devices needed are accounted for.
Even a security team solely of one person at the front desk can execute all actions necessary to resolve situations occurring in the advanced layers of security with the right configuration of security tools.
Automation Saves Time and Resources
Once the resources have been identified, planning for automations is the next critical step in the process. Automations allow for limitations to be addressed, while defining who will receive which notifications and which medium will be used for delivery.






